Also see the dedicated surgemail.com website with knowledge base and ticketing system
Configuring 'Proxy Mode Clusters'
This systems allows both infinite scaling, and 3 layer security. The incoming POP/SMTP connections arrive at one of several front end 'proxy' servers (running SurgeMail in proxy mode) these servers then lookup the user in the networked user database (via LDAP or our own TCPAuth module) and along with the normal response an extra response code of 'tohost=backend.host.name' is returned, the proxy then redirects the user to the appropriate back end system.
So you might run 4 back end systems, each with 100,000 users, and 2 front end systems. To add more users you just add as many front end and back end servers as needed to cope with the load.
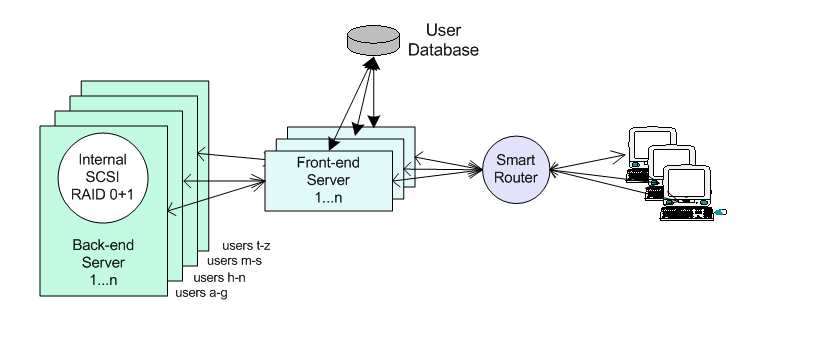
Each user is only on one of the back end systems, the only piece in the system that has to handle all the users is the user database, which is a relatively trivial task as the quantity of data per entry is so small. We recommend the use of NWAuth or LDAPAuth but any of the database back end authent modules would be suitable.
See here for technical details
Note: 3 Layer Security: This model is called '3 layer security' as the front and back end systems can be separated by another fire wall. And in the case of 'WebMail' the user web interface can also be separated from the front end systems by a fire wall, hence '3 layer' :-)
To implement this system set on the proxy system the setting g_proxy true, and in the authent module add the 'tohost=xxx' field. For existing user accounts you can define g_proxy_default host.name so that user records with no 'tohost' entry are correctly sent to the existing back end system. In this way a non proxy based system can be instantly turned into a proxy based system.